
Corporate laptops on Windows 10 can now be managed and secured more easily. Instead of joining an Active Directory domain or installing a management client, Microsoft leveraged mobile device management (MDM) based on the Open Mobile Alliance (OMA) specification. With Windows 10 MDM based on an open standard, there are a number of tools that can manage Windows 10 computers, including AirWatch, MobileIron, and Microsoft’s own Intune. This series will demonstrate a Windows 10 MDM implementation with Intune, but the same concepts can be translated to any number of enterprise mobility management systems.
Intune is an integrated part of the Office 365 suite of products and therefore makes for a great solution for existing Office 365 customers looking to deploy a MDM solution. For this blog post, we will assume a scenario with an Office 365 customer who currently manages Windows 10 machines with Group Policy in an Active Directory domain that is syncing to Azure AD. Our Windows 10 MDM implementation needs to meet the following objectives to replace the controls in the current imaging and Group Policy implementation:
Run on any Windows 10 PC out of the box
Add local admin rights for desktop administrators
Require BitLocker encryption and backup BitLocker keys
Manage Windows Updates setting by user group
Upgrade the Windows license to Enterprise
Deploy a SCEP certificate for WiFi access
Deploy Office 365 ProPlus
Deploy a set of custom fonts
Allow users to access several office printers
In this section we will cover how to:
Run on any Windows 10 PC out of the box
Add local admin rights for desktop administrators
Require BitLocker encryption and backup BitLocker keys
Configure Azure AD and Intune for Windows MDM
First, we need to tell Azure AD that we want to use Intune for MDM by going to the Azure Active Directory blade in the Azure portal, selecting Mobility, then Microsoft Intune and setting the MDM user scope to Some or All. If you are setting up Windows 10 MDM in a production tenant, it is recommended that you set up a test group to apply MDM policy to while testing.
Now users could use the URLs listed on the Configure page to register devices with Intune but we can set up CNAME DNS records that will automate the enrollment process. Details for both of these steps can be found in the Microsoft documentation, set up enrollment for Windows devices.
Add Local Administrators
While we are still in the Azure AD blade, we can go to Devices, then Device settings to add additional administrators to the Local Administrators group on Azure AD joined devices. Select the Selected button next to Additional local administrators on Azure AD joined devices and select the additional users who should be set up as local administrators. The reason “additional” is used in this setting is because Global Administrators and device Owners are set up as Local Administrators by default. If your needs require that the device Owners not be administrators, take a look at Windows Autopilot deployment profiles, which just came out of preview as I was writing this.
BitLocker
If the device supports it, Azure AD will automatically enable BitLocker and backup the BitLocker key in Azure AD, however a number of devices don’t support automatic BitLocker encryption, so we will also include an Intune Compliance policy that requires BitLocker encryption and a password for all users on the device.
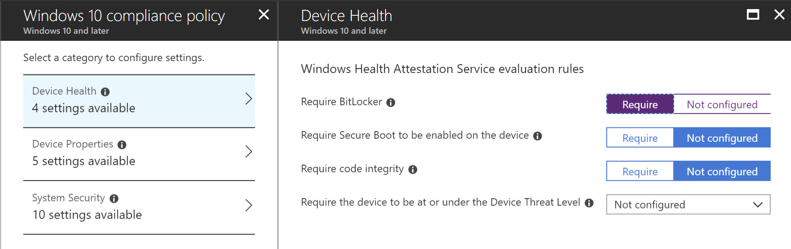
Figure 1. Compliance Policy – Require BitLocker
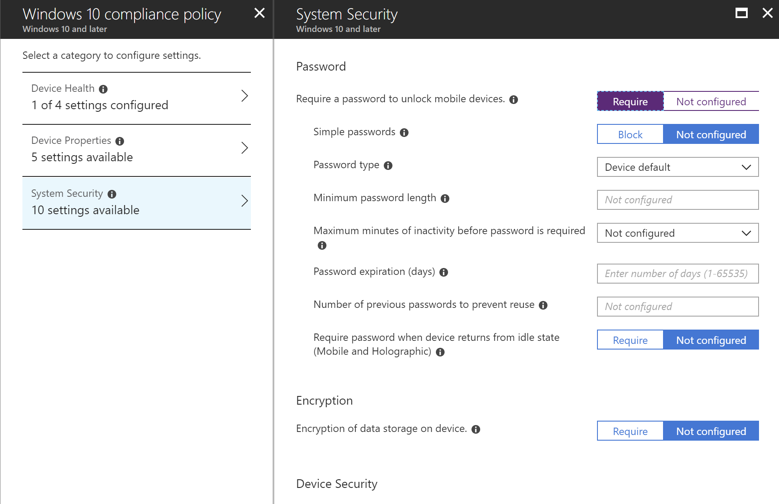
Figure 2. Compliance Policy – Require a Password
Users whose devices are not automatically encrypted are prompted to encrypt their device after it is joined to Azure AD and the Intune Compliance policy is applied. This interactive process prevents users from accidentally having their disk encrypted and locked without having the BitLocker key backed up.
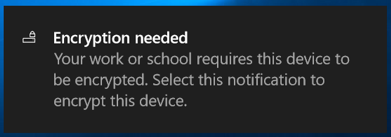
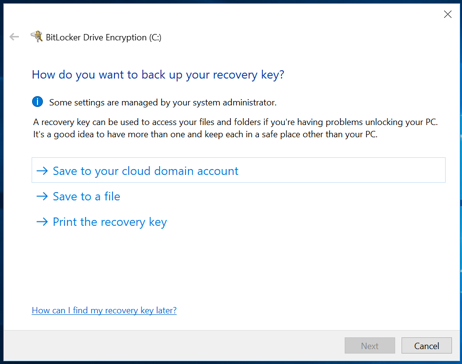
Figure 3. End User Encryption Walk-through
Once the BitLocker key is backed up in Azure AD, users can find their own keys in the Profile section of the myapps.microsoft.com portal. Administrators can see the BitLocker key in the Device blade in Azure AD.
Moving Forward With MDM
The second part of this series will cover how to:
Manage Windows Updates setting by user group
Upgrade the Windows license to Enterprise
Deploy SCEP certificate for WiFi access
Do you have questions about creating a MDM Windows 10 deployment to meet your needs? Credera has expertise helping clients achieve modern deployment patterns that can streamline the deployment process, freeing up resources from time-consuming image deployment processes. We would love to discuss potential cloud and infrastructure solutions with you—contact us at marketing@credera.com.
Contact Us
Let's talk!
We're ready to help turn your biggest challenges into your biggest advantages.
Searching for a new career?
View job openings