
Do you save passwords in your browser so they can automatically be filled in for you every time you sign into a website? I used to think this was a great idea and huge time saver since it is a good security practice to not use the same password for everything, yet trying to remember multiple passwords can be a pain. With companies integrating more online services into their daily operations, users storing their passwords in a browser may save time and be convenient—but is not best practice when it comes to corporate data security. Here are a couple of reasons why:
If a user’s computer is ever compromised and accessed remotely over the internet by an unauthorized party, the unauthorized party will have immediate and complete access to the user’s online accounts if the passwords have been stored locally.
Unauthorized parties could also be internal as well, so storing passwords will make the user’s online accounts vulnerable to anyone who has access to the user’s computer if left unlocked while unattended. Yes, people still walk away from their computers leaving them unlocked. I see it in corporate environments more often than I would like.
How Easy It Is to Get Passwords From a Browser
Now, let me show you how easy it is to reveal a user’s saved password from within a browser. I will be using Chrome in my example but the same principle applies to Internet Explorer and FireFox.
Here is a site where I have my login info saved into the browser for the purposes of this demo. As you can see, the password is being masked by dots.
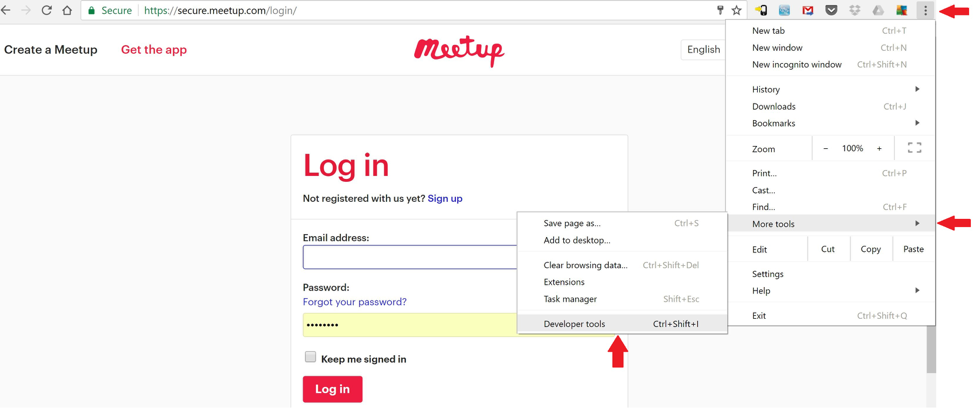
Click on the three vertical dots at the top right of the Chrome browser, then navigate down to More tools > Developer tools and click on Developer tools.
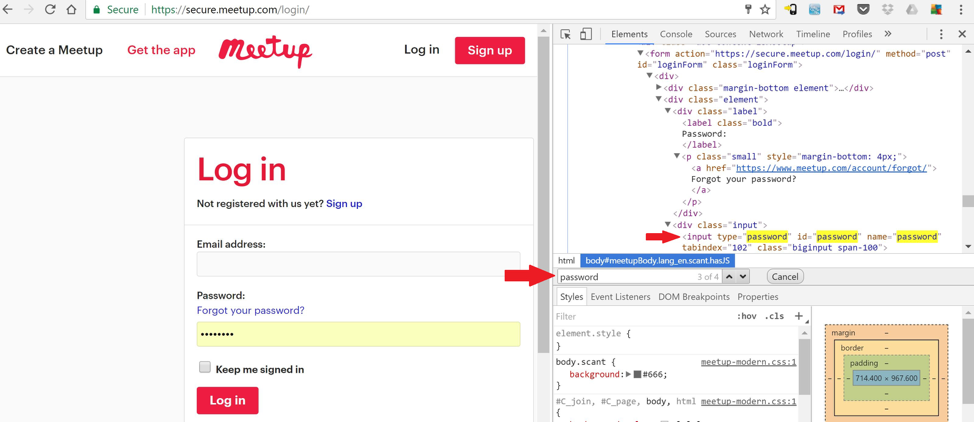
From here you will look for a line beginning with <input type=”password”. You can also press Ctrl+F to search for specific text, type in “password”, then press Enter, and you will be taken to any instance of the word.
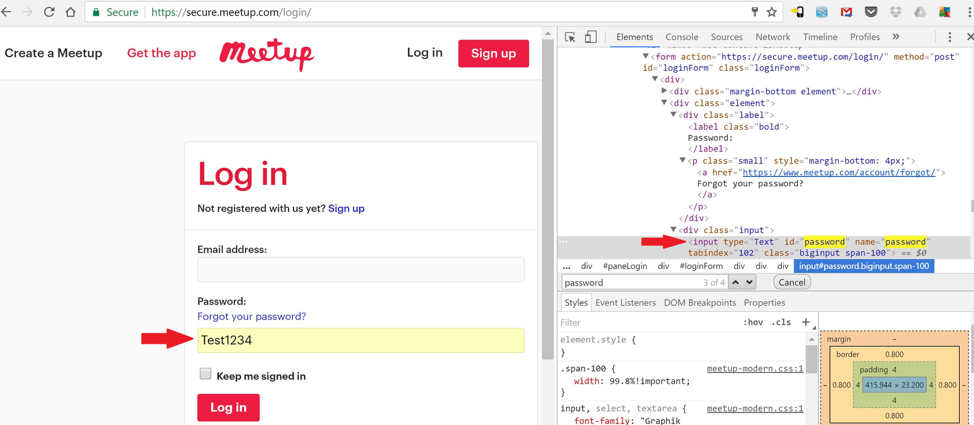
Now that the line beginning with <input type=”password” has been found, double click on “password”, change it to “Text” like above, then press the Enter key and voila! The password being masked by dots has now been changed to plain text revealing your password.
Yes, it really is that simple.
However data security or any kind of security for that matter is all about leveraging multiple layers of defense. If a user’s computer is locked, an unauthorized party has a layer of security to get through that could deter someone with physical access to the machine. As for unauthorized access via the internet, having multiple layers of security like hardware/software firewalls, anti-virus protection, intrusion detection/prevention systems, and so on are all layers of security to detect and/or deter unauthorized access. Not allowing users to save their passwords within a browser is another layer that should be considered when developing your company’s information security policy.
Extra Security With Password Managers
Some users prefer to use a password manager for an extra layer of security. Password managers typically come in two forms, online or cloud-based such as Lastpass and offline or local such as 1Password. The difference between the two comes down to the storage location of your encrypted password database, online or offline. Whether online or offline, it really comes down to personal preference as well as the features offered.
With online password managers there is always the risk of a compromise since the data is being saved in the cloud. That being said, the passwords are encrypted and there are multiple layers of security including two-factor authentication and security alerts to minimize risk. Online password managers usually have a mobile application as well that will integrate with your mobile device, a feature you would not get with an offline password manager.
On the other hand, offline password managers do exactly that, store your passwords locally on your machine. The data is encrypted and has two-factor authentication like its online counterpart, minus the risk of a compromise in the cloud.
I would recommend trying both options in order to provide more insight into which option would work best for you.
Ready to Improve Your Security?
Are you interested in adopting a security policy that effectively incorporates information security best practices? Credera has extensive experience in helping clients develop security policies that balance the concerns of end user productivity and protection of corporate data. If you have questions or would like to discuss information security solutions, contact us at sales@credera.com .
Contact Us
Ready to achieve your vision? We're here to help.
We'd love to start a conversation. Fill out the form and we'll connect you with the right person.
Searching for a new career?
View job openings