
It is time to accept the difficult truth that no environment is immune to determined hackers eager to get their hands on whatever data they can. What is worse, security strategies have become a cat-and-mouse game. As the technology and methods used to prevent breaches improve, so do the methods and technology attackers use to get in. In the past five years alone, we have seen companies such as Equifax, JP Morgan, Yahoo, and Target become the victims of cyber-breaches that exposed sensitive information related to billions of individuals. Without weighing the merits of said companies’ security practices, it is safe to assume each of them implemented processes to keep attackers out. While concentrating processes on keeping unauthorized actors out is imperative, it is no longer enough for a robust security strategy that addresses the ever-changing challenges we face today.
By accepting the possibility that an environment breach will always exist, focus can be shifted toward designing back-end resources that slow down the flow of sensitive data being retrieved by the attacker. In other words, if they are going to get in, let’s extend the time it takes for them to leave with anything of value.
Dropping an Anchor
While details are limited for exactly how the previously mentioned breaches took place, the general understanding is that they all followed a similar process. An attacker gains access to a front-end server, which is used to extract data from a back-end application database. This permits the attacker to then leave and work on cracking any hashed data from wherever they please. The process allows for the extraction of large data sets in a relatively short amount of time, possibly preventing any corrective actions to be taken before the attack is over.

Diogo Mónica, security lead at Docker, recently presented a concept called “crypto anchoring,” which would disrupt that process. Diogo defines a crypto anchor as “a service that forces a data-flow to only be available within the boundaries of your infrastructure.” These anchors prolong the time an attacker would need to spend within your environment extracting useful data, increasing the chance of detection and leaving better details as to what data was accessed.
A practical way to implement a crypto anchor in your environment is through the use of a hardened physical device used for key storage and cryptographic operations, known as a Hardware Security Module (HSM). The keys stored by the HSM and the crypto-processes it performs solely reside within the device, providing physical and logical security. Developing an application or database that is dependent on a HSM for key management and cryptography prevents stored data from being useful outside the environment where the HSM is located.
Instead of an attacker extracting a large amount of unencrypted or hashed data in a short amount of time, they would be forced to wait on the HSM to decrypt the data piece by piece. In doing so, the HSM is effectively “anchoring” them until the job is complete. This may only add milliseconds per request, but those add up as the data set grows. An attack that may have lasted an hour originally, could be drawn out over several hours or days. Additionally, thresholds could be set that would throttle requests the HSM accepts, further increasing time and possibility of detection.

As more businesses are taking advantage of AWS cloud services every day, some may wonder if implementing crypto anchors is still a solution they could benefit from. The answer is absolutely, and as with most cloud solutions, it can increase its functionality.
AWS CloudHSM
AWS takes the existing benefits a HSM provides and adds additional functionalities to make it a powerful cloud service. CloudHSM is a fully managed on-demand HSM, utilizing dedicated FIPS 140-2 Level III certified modules for use in the AWS cloud. AWS takes care of provisioning, patching, high availability, and backing up the HSM, while never having access to anything stored on it. CloudHSM is provisioned directly to your Virtual Private Cloud where, via strong authentication, you have sole administration over the keys stored on the device and how resources are allowed to interact with it. Storing keys and using them for crypto-processing are all done within the device, where root trust resides at the physical level.
You can take advantage of CloudHSM when developing your applications through the use of industry-standard API programming languages, including PKCS#11, Java Cryptography Extensions, and Microsoft CryptoNG libraries. There is also some native integration support for AWS resources utilizing Oracle, SQL, or Apache.
After integrating CloudHSM into your AWS environment, the additional benefits come through the ability to monitor the service in Amazon CloudWatch, a powerful monitoring platform. CloudWatch can take metrics made available to it and turn them into automated responses. For example, if you know the average number of decrypt requests your HSM might receive per day, you could set an alarm in CloudWatch to react when that number is exceeded. The response could be as simple as using Amazon’s Simple Notification Service (SNS) to send you an email, or as complex as invoking a function in AWS Lambda, a serverless compute resource, to terminate decrypt requests from the offending application source.
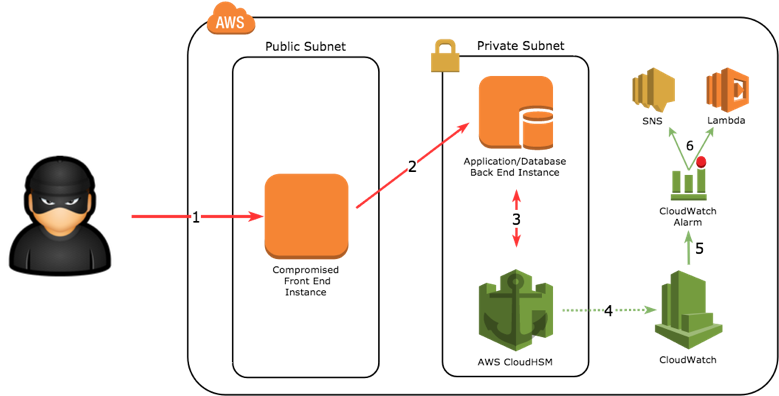
The above illustration represents how this process would work:
An attacker gains access to a front-end instance
The attacker uses the compromised instance to retrieve data from a back-end database instance
As the database uses CloudHSM for key storage, it must send decrypt requests for each item
CloudHSM is sending metrics to CloudWatch for monitoring
The set threshold for decrypt requests is exceeded and CloudWatch produces an alarm
The alarm uses SNS to send an email to designated individuals and invokes a Lambda function to terminate decrypt requests from the database instance
By using CloudHSM in parallel with CloudWatch, you can establish an effective crypto anchor to slow down the exfiltration of data and take remediating actions as soon possible.
Interested in Learning More?
If you want to learn more about better securing your on-premise and cloud environments utilizing crypto anchors or any other method, Credera has an extensive history of helping our clients adopt best security practices throughout their infrastructure. Effectively responding to evolving security challenges can be demanding, and we would love the opportunity to answer any questions you may have or assist you in any way we can. Feel free to contact us at marketing@credera.com. Anchors aweigh!
Contact Us
Let's talk!
We're ready to help turn your biggest challenges into your biggest advantages.
Searching for a new career?
View job openings