Technology
Feb 24, 2022
Demystifying Microsoft 365 Cloud Security Part 1: Identity and Access Management

Cloud security is a top concern for organizations starting their cloud adoption journey. Microsoft 365 offers many security options, including solutions that span the breadth of their enterprise cloud ecosystem. The sheer number of licensing options makes it easy to find yourself down a rabbit hole of management portals.
The goal of this article is to reduce the confusion and shed light on the various security features within the Microsoft 365 world.
Microsoft has designed its cloud security solutions around four foundational components: identity and access management, threat protection, information protection, and security management. This article covers the first, identity and access management, in Credera's four-part series.
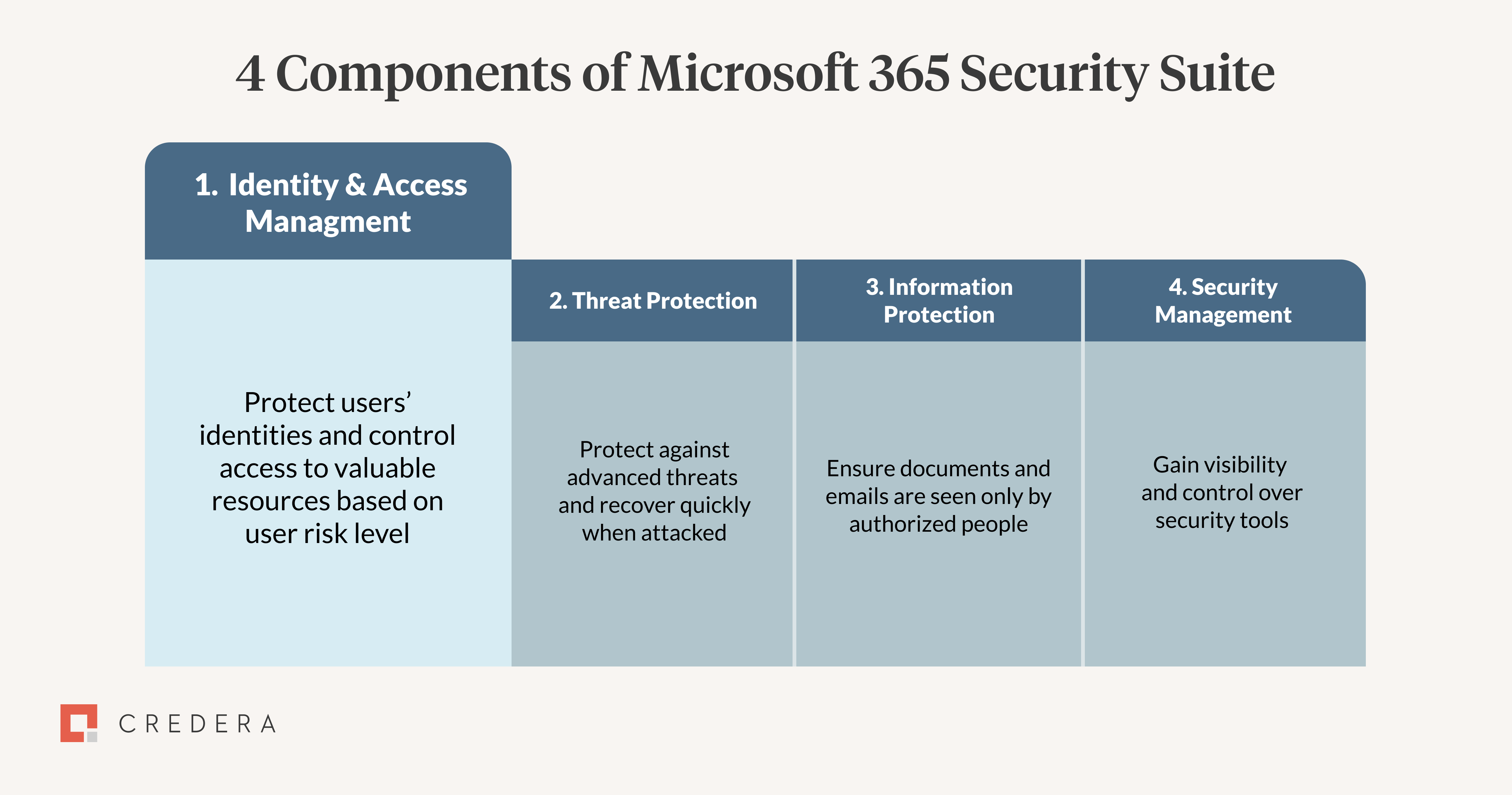
Figure 1: Four components of Microsoft 365 Defender security suite.
What Is Microsoft’s Approach to IAM?
Azure Active Directory (AD) is Microsoft’s cloud-based identity and access management (IAM) solution. It allows organizations the ability to manage digital identities, roles, and control access to enterprise and cloud resources. Identities can be user, device, or application-based objects.

Figure 2: IAM layers of protection.
Why Use IAM for Cloud Security?
The primary goal of an IAM solution is to provide secure access to users and devices. However, traditional physical perimeters are becoming obsolete. More organizations have moved to remote work over the past year due to the COVID-19 pandemic, so companies are looking for a better way to manage, control, and secure access from anywhere and across multiple devices. IAM solutions provide a means to improve security by using several access controls.
Some benefits of an effective IAM solution include:
Multi-factor authentication (MFA) – Privileged accounts such as the Azure AD global administrator should be tightly controlled and monitored. Access controls to these powerful accounts can be bolstered with MFA and monitored using sign-in risk policies.
Policy-based access – Azure AD uses role-based access control (RBAC) to follow the principle of least privilege, which limits resource access only to those users or groups granted access by the assigned role.
Zero-trust policy – This is based on the principle of verified trust. To gain access, an identity must be verified. This can be done using tools like Conditional Access to enforce two-factor authentication or verify the connecting device complies with enforced policies.
Centralize identity management – Identities can be synchronized between on-premises and cloud directories. This synchronization streamlines access across multiple platforms and applications using single-sign on (SSO). Common policies and security controls can be enforced across different identity types including application secrets and API keys.
Improve compliance – Many organizations are required to meet specific industry or government regulatory compliance standards. When deployed successfully, IAM solutions play an integral role in compliance by allowing organizations to implement security controls to meet those requirements while easing the reporting burden for compliance teams and administrators alike.
Azure AD Security Features in Microsoft Cloud Security
Microsoft’s zero-trust model starts with Azure AD. Built-in security controls work together to provide strong access protection and reduce the attack surface. We’ll highlight four key features Azure AD provides to improve cloud security at the perimeter.
1. Azure AD Conditional Access – Conditional Access policies leverage granular controls to permit or deny access based on specific criteria. Policies can enforce MFA when logging in from an unfamiliar location or deny access altogether based on the type of device used. An example might be a “jail broken” iPhone or a device connecting from a foreign country. Conditional Access policies work in conjunction with many other Microsoft cloud security solutions such as Intune MDM and Microsoft Cloud app security.
2. Multi-factor authentication – Azure AD MFA provides an additional layer of security by enforcing a second form of authentication. Administrators can leverage a few different authentication methods in addition to an individual’s standard username and password.
Verification code through a mobile app – An OAUTH code generated on a mobile app such as Microsoft Authenticator is used to verify log in.
Notification through a mobile app – Push notifications sent through an authenticator app must be approved to allow log in.
Call to phone – An automated voice call is placed to the user’s registered device verifying the log in.
Text message – A text message containing a verification code is sent to the user’s registered device, which is then used to verify log in.
3. Privileged identity management (PIM) – PIM is a feature used to protect privileged access. In Microsoft 365 and Azure, there are many defined administrative roles and access to any privileged role can leverage PIM. Time-bound access, also known as just-in-time (JIT) access, can be granted to a privileged role, or used to gain access to specific cloud resources. Mechanisms can be put in place requiring approvals or justification for access and an audit trail can be created when access is activated.
4. Defender for Identity – Formerly knowns as Azure AD Advanced Threat Protection, this is an advanced security solution that can be used to monitor both cloud-based and on-premises authentication events. This solution is used to identify and detect log in risks and unusual behavior, such as impossible travel type scenarios or potentially compromised credentials.
Implementing IAM Solutions for Microsoft Cloud Security
Implementing IAM solutions can be challenging enough, but it’s still easy to get overwhelmed with the many features offered through Microsoft 365. We recommend reviewing the security features available through Microsoft 365 and look to enable these features in your tenant to provide improved and more secure access controls.
In this blog series, we hope to demystify the tools that comprise the Microsoft 365 security suite while providing some insight through our experiences. In the next post, we’ll cover Microsoft’s second foundational security pillar, threat protection, and the security solutions that encompass it.
Need a Guide for Your Cloud Transformation Journey?
Credera is passionate about helping organizations foster cloud enablement that drives successful cloud adoption and valuable business outcomes. Our unique expertise in corporate strategy, innovation, and application development enables us to bring a holistic approach to your cloud adoption journey.
Explore Credera’s Cloud Transformation Framework to learn more, or reach out to us at marketing@credera.com if you have questions or would like to discuss cloud and infrastructure solutions.
Contact Us
Let's talk!
We're ready to help turn your biggest challenges into your biggest advantages.
Searching for a new career?
View job openings




